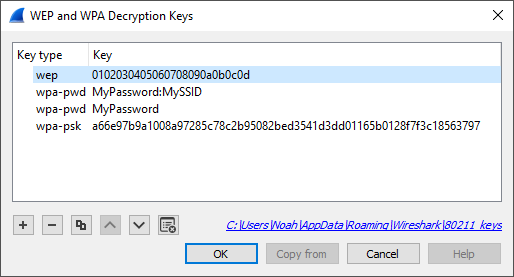
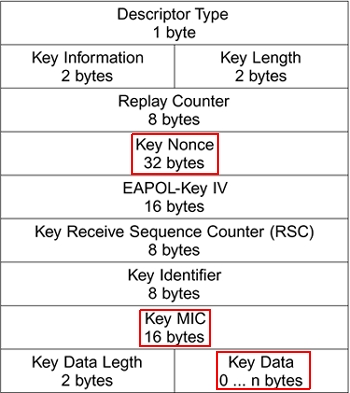
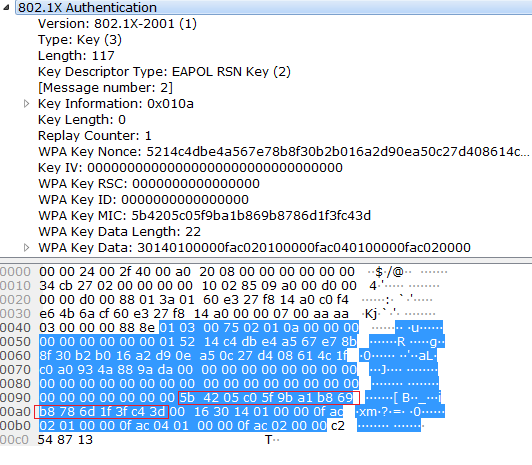
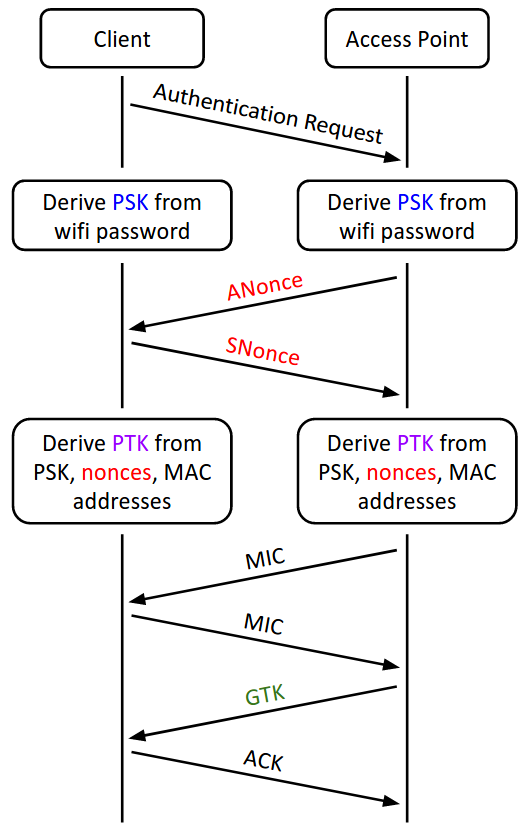
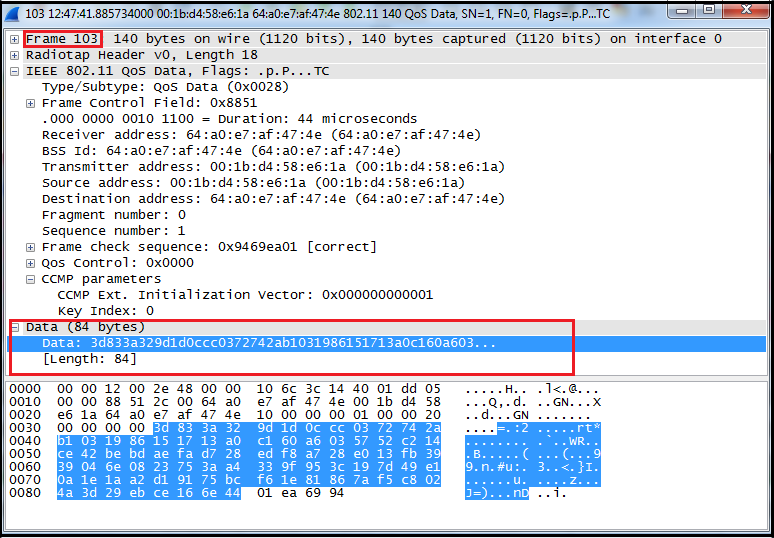
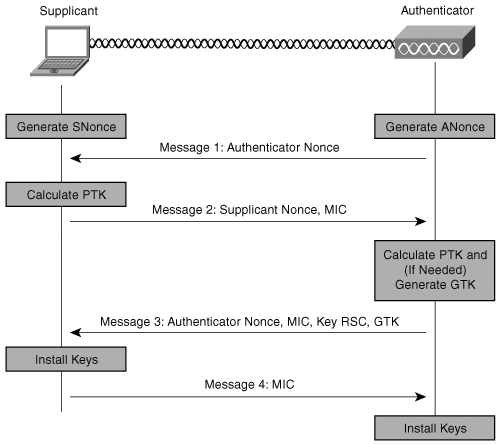
First Message of the WPA Four-way Handshake (ANonce and AP MAC Address)... | Download Scientific Diagram

penetration test - can an attacker find WPA2 passphrase given WPA key data and WPA MIC - Information Security Stack Exchange

pbkdf2 - WPA/WPA2 Handshake -- A question on the computation of the MIC - Information Security Stack Exchange






![Capturing WPA/WPA2 Handshake | Cracking Principles [CYBERPUNK ] Capturing WPA/WPA2 Handshake | Cracking Principles [CYBERPUNK ]](https://cdn.cyberpunk.rs/wp-content/uploads/2019/06/Capturing_WPA_WPA2_Handshake_bg.jpg)