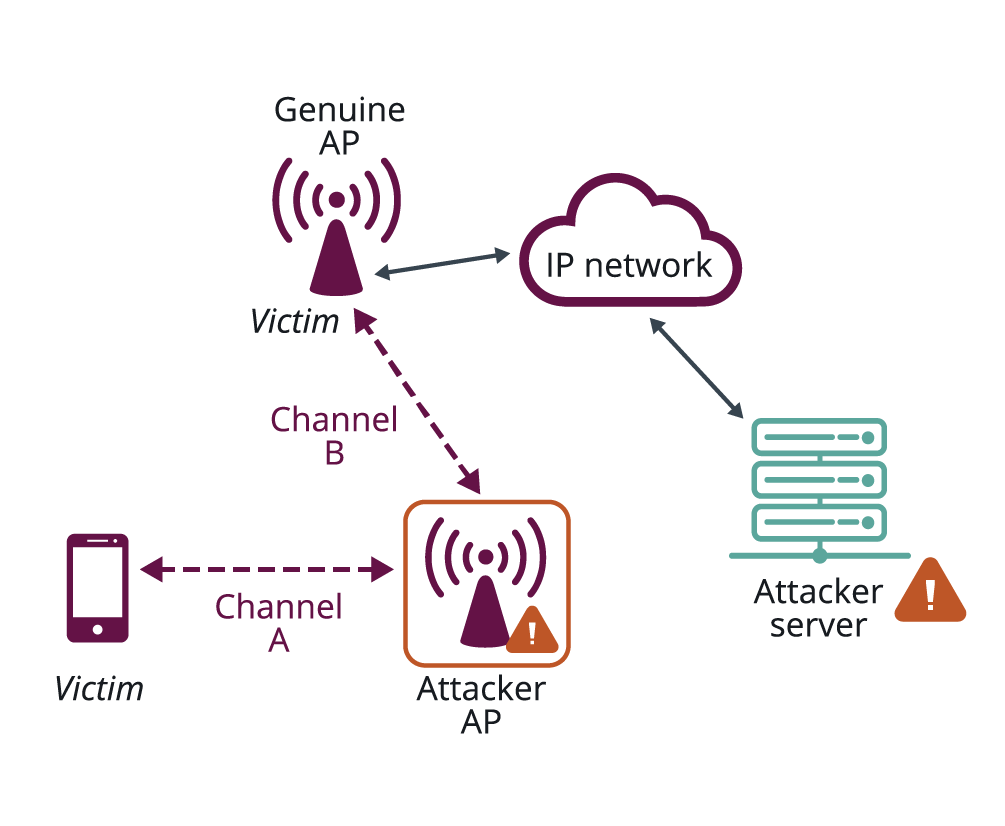
Wi-Fi CERTIFIED WPA3™ December 2020 update brings new protections against active attacks: Operating Channel Validation and Beacon Protection | Wi-Fi Alliance

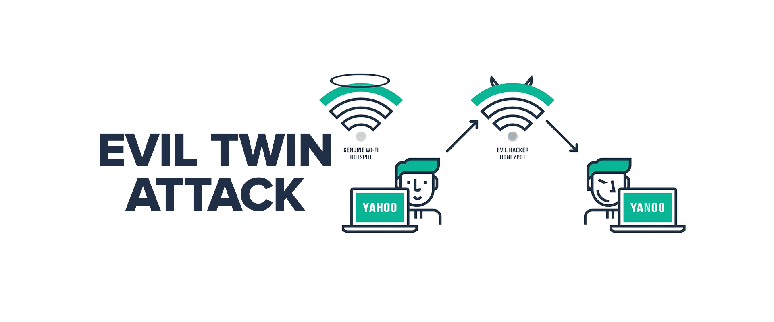
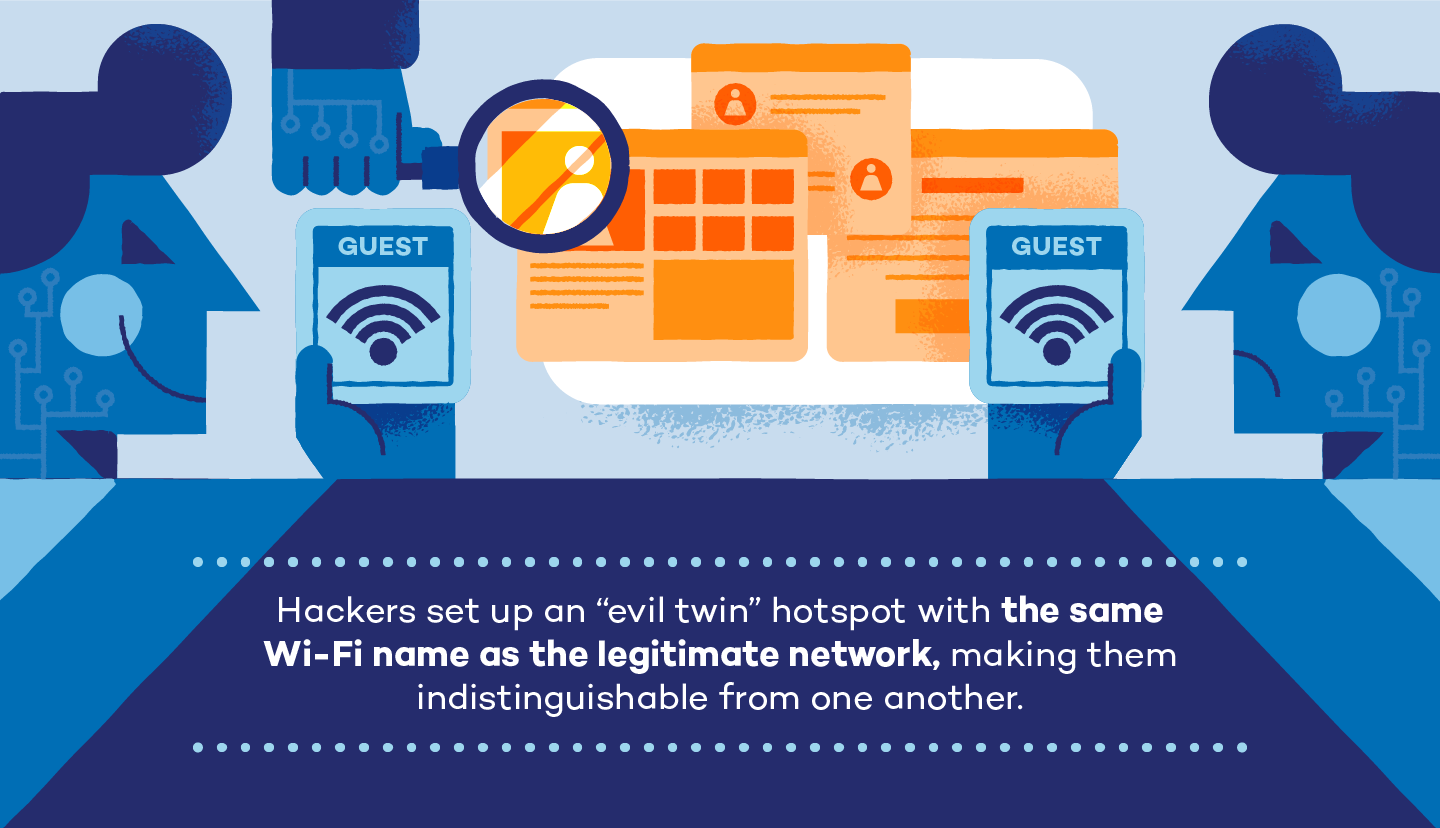
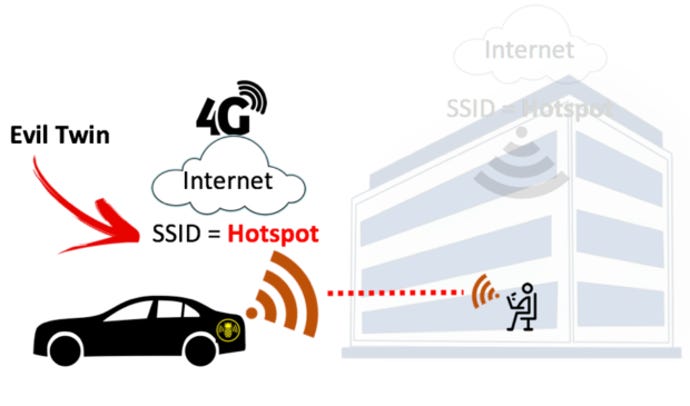
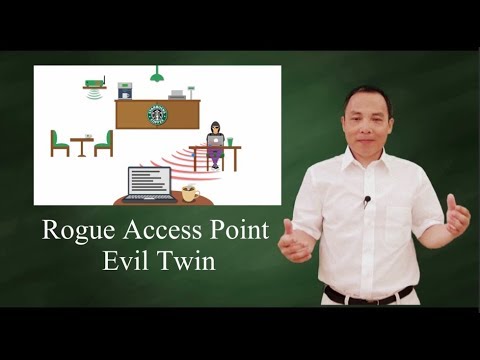
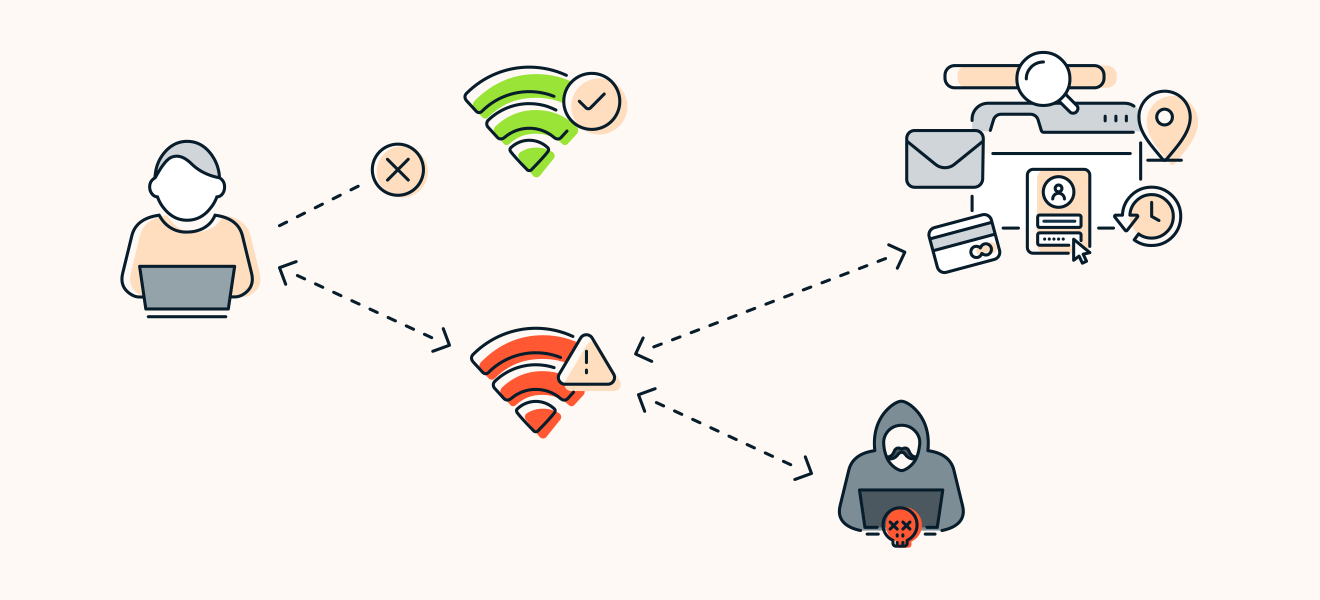
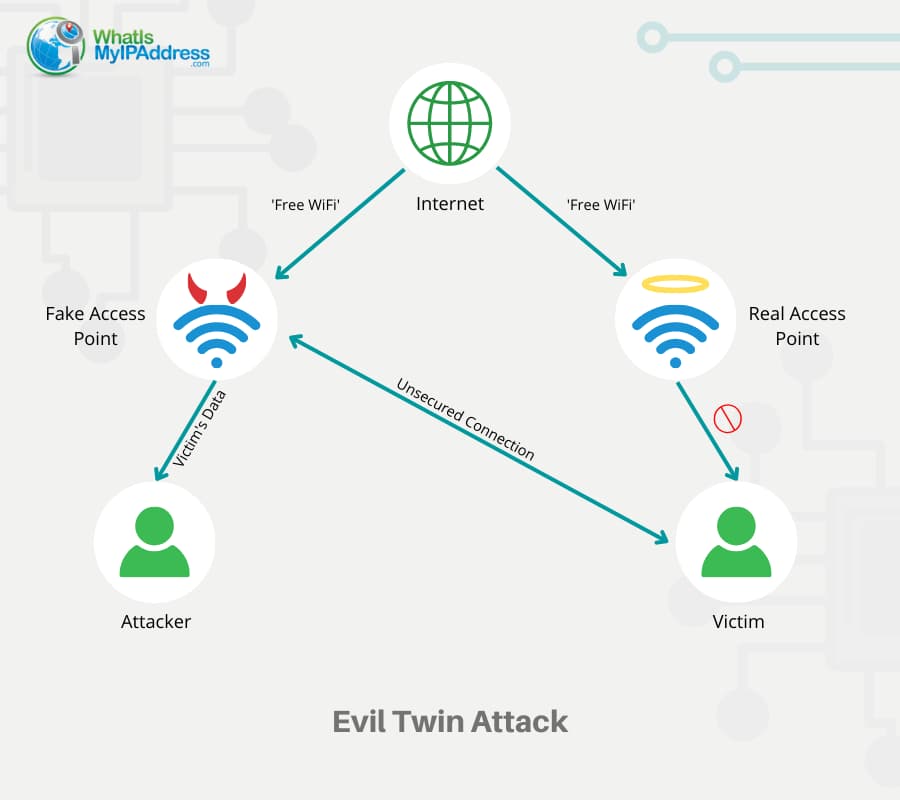
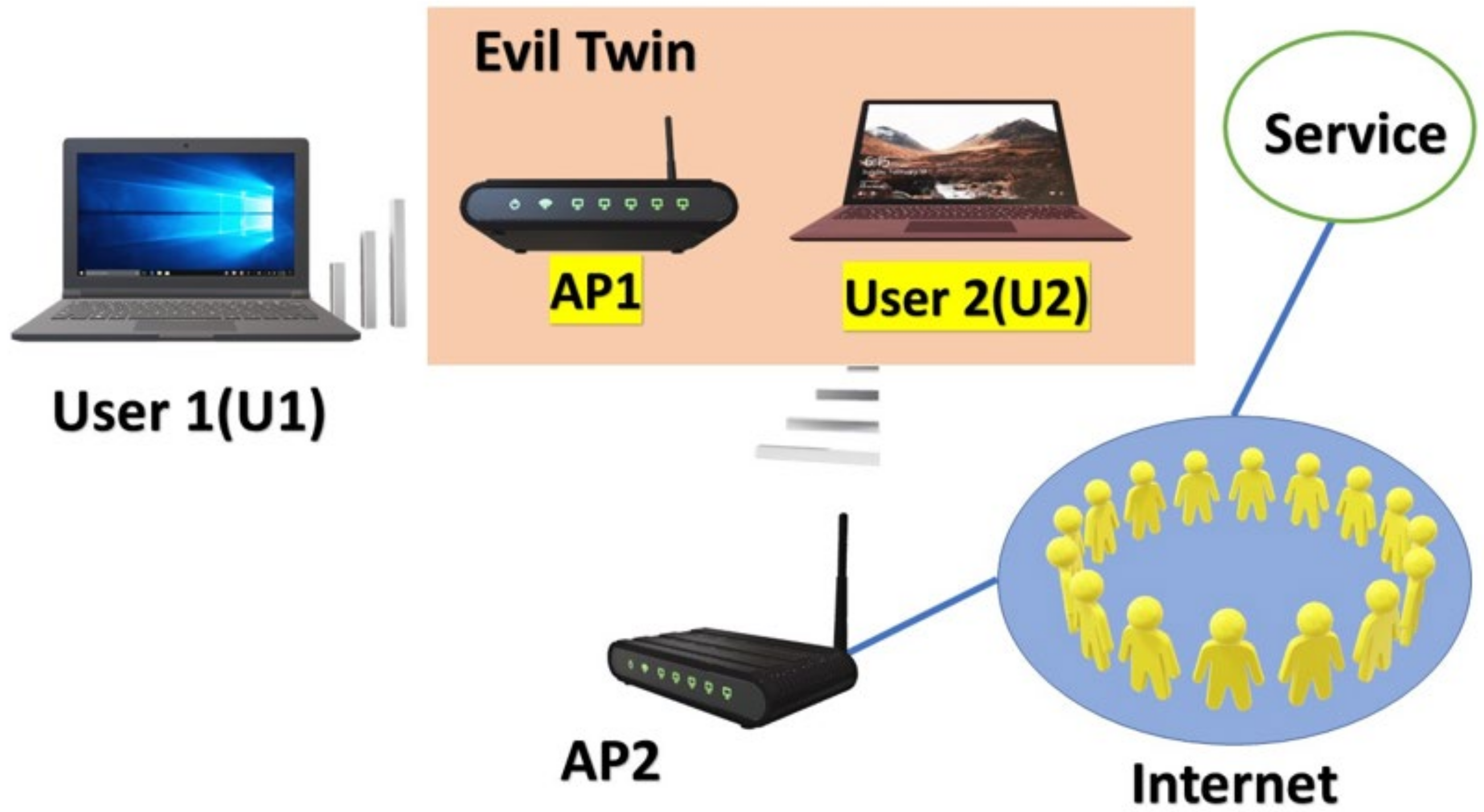
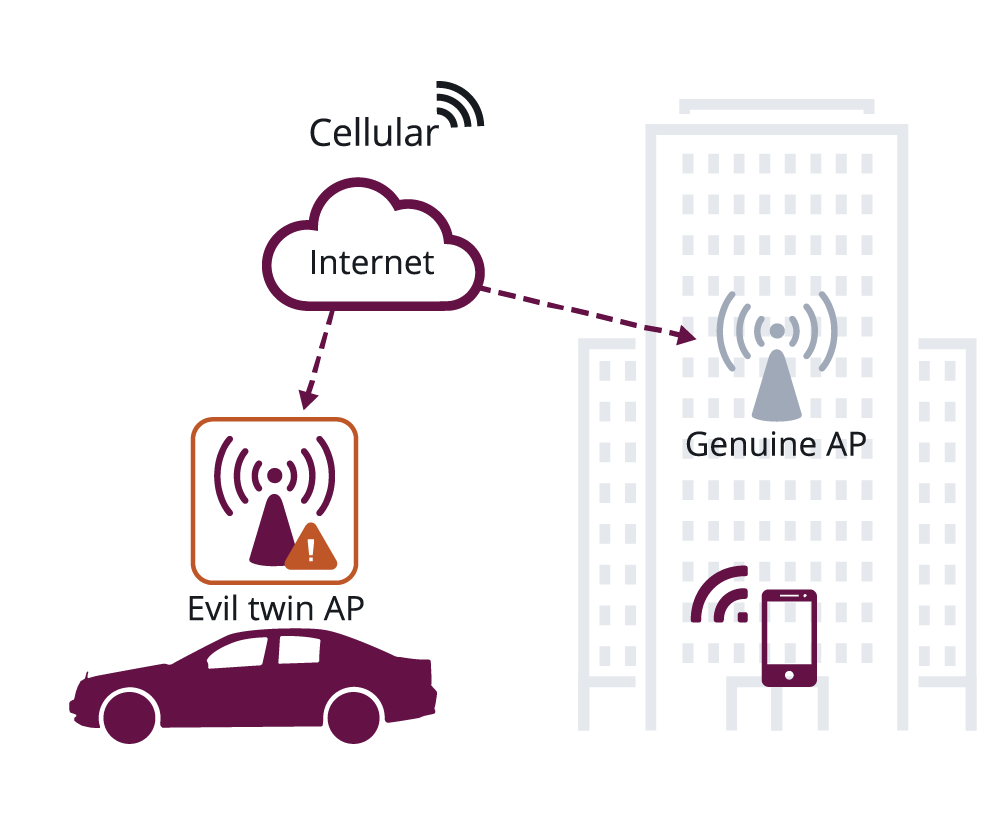
Digimune - What is an "Evil Twin Attack"? An evil twin attack is fake Wi-Fi network which a hacker sets up and looks like a legitimate access point. The evil twin wireless

A passive user‐side solution for evil twin access point detection at public hotspots - Hsu - 2020 - International Journal of Communication Systems - Wiley Online Library

Intrusion detection system for detecting wireless attacks in IEEE 802.11 networks - Sethuraman - 2019 - IET Networks - Wiley Online Library